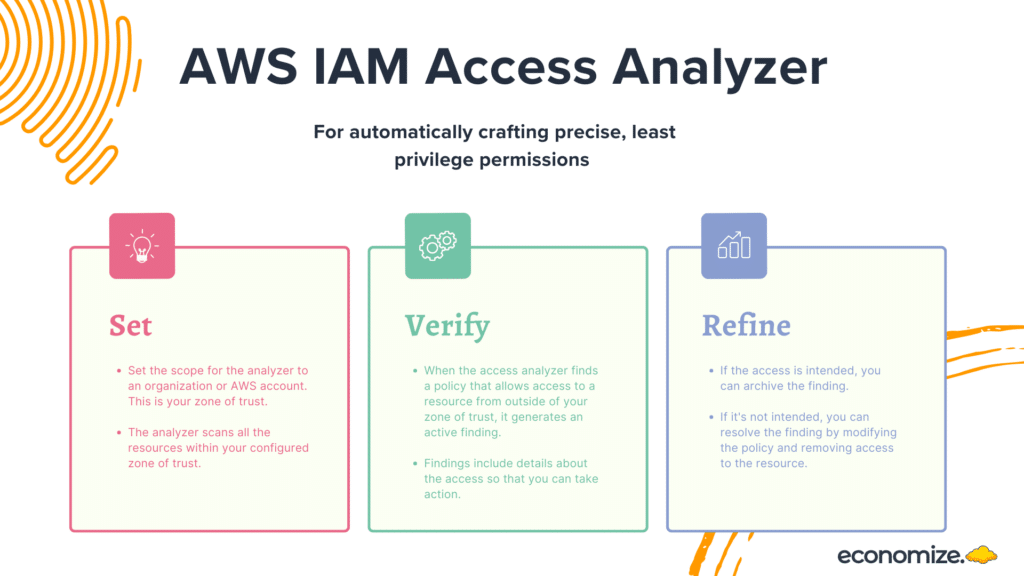
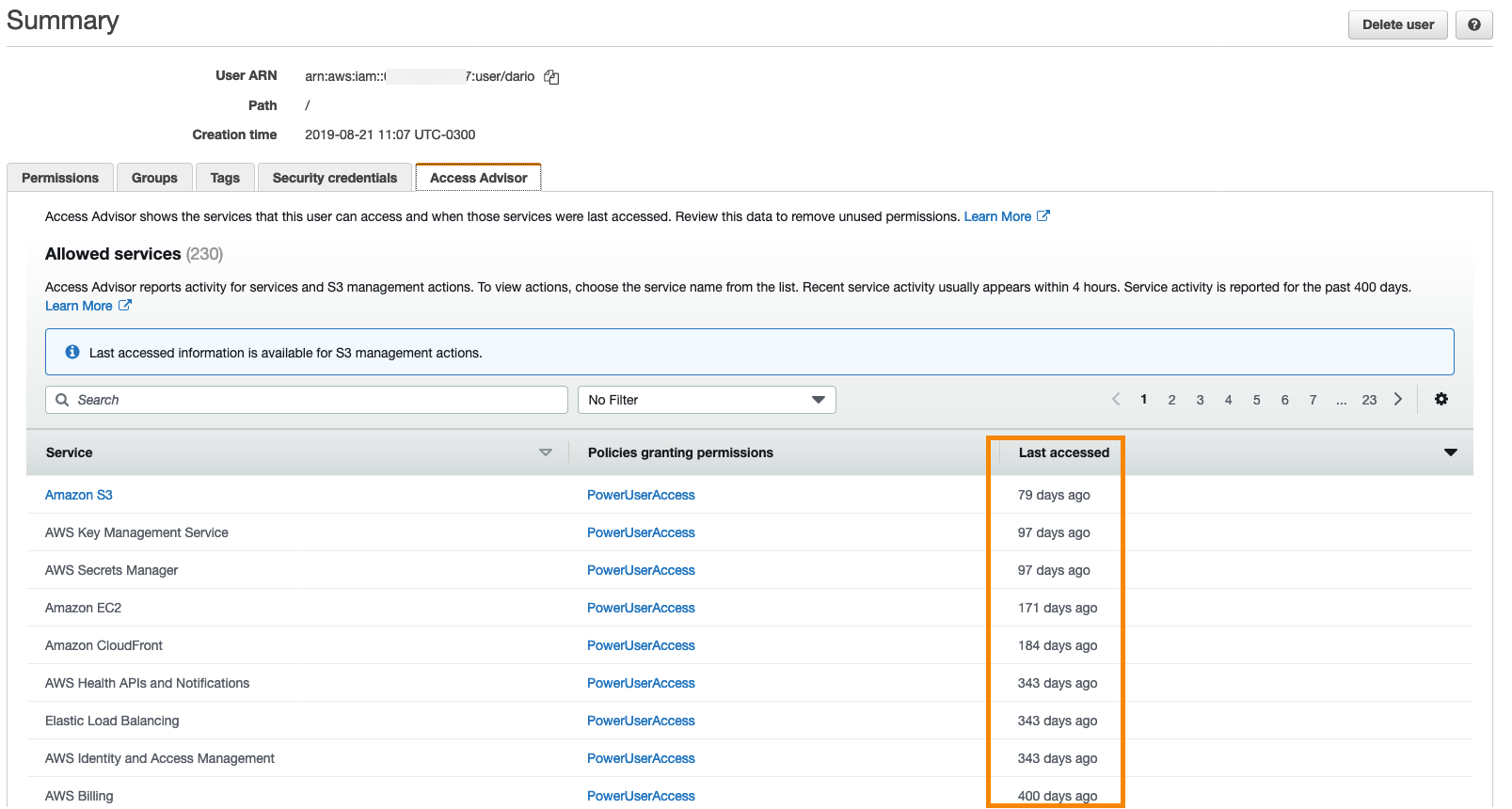
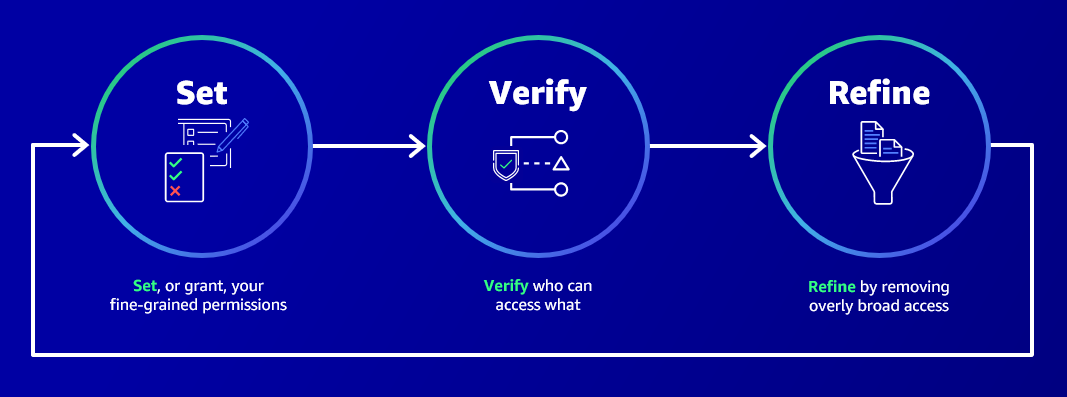
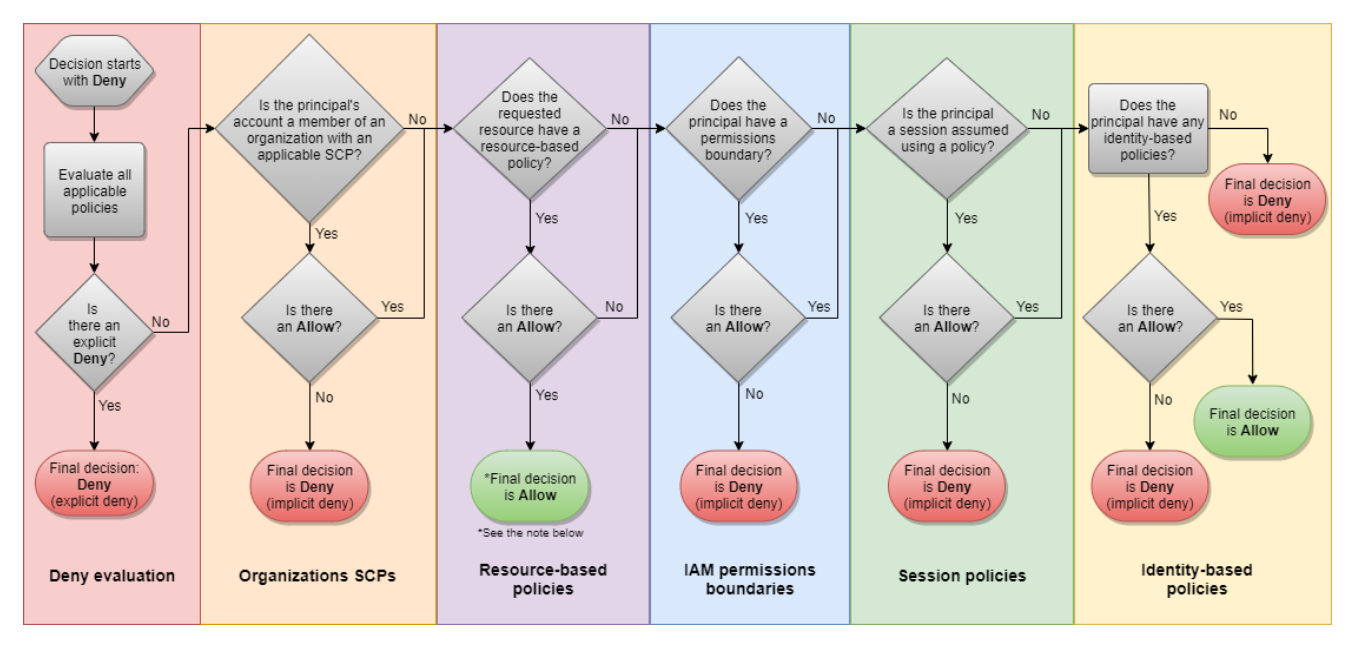
IAM Access Analyzer makes it easier to implement least privilege permissions by generating IAM policies based on access activity | AWS Security Blog

How to Minimize Unintended Access and Achieve Least Privilege with Ermetic and AWS | AWS Partner Network (APN) Blog
Cloudsplaining, AWS IAM Security Assessment tool that identifies violations of Least Privilege and generates a risk-prioritized HTML report with a triage worksheet. : r/netsec

Continuous permissions rightsizing to ensure least privileges in AWS using CloudKnox and AWS Config | AWS Cloud Operations & Migrations Blog
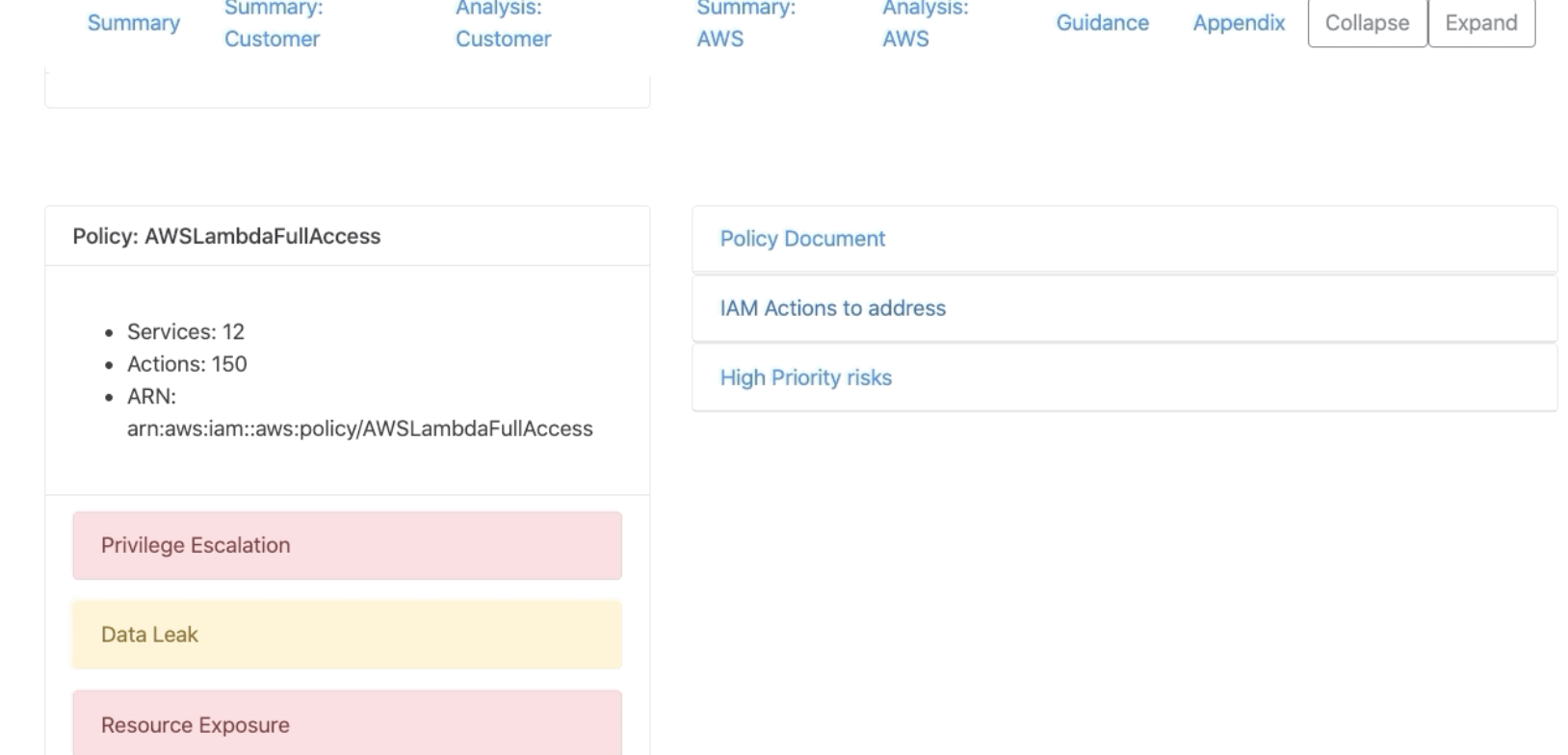
Cloudsplaining - AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized report.

IAM Access Analyzer makes it easier to implement least privilege permissions by generating IAM policies based on access activity | AWS Security Blog