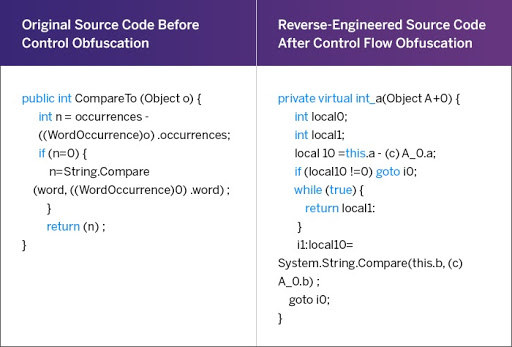
Example of lexical obfuscation: (a) obfuscated snippet; (b) target code... | Download Scientific Diagram

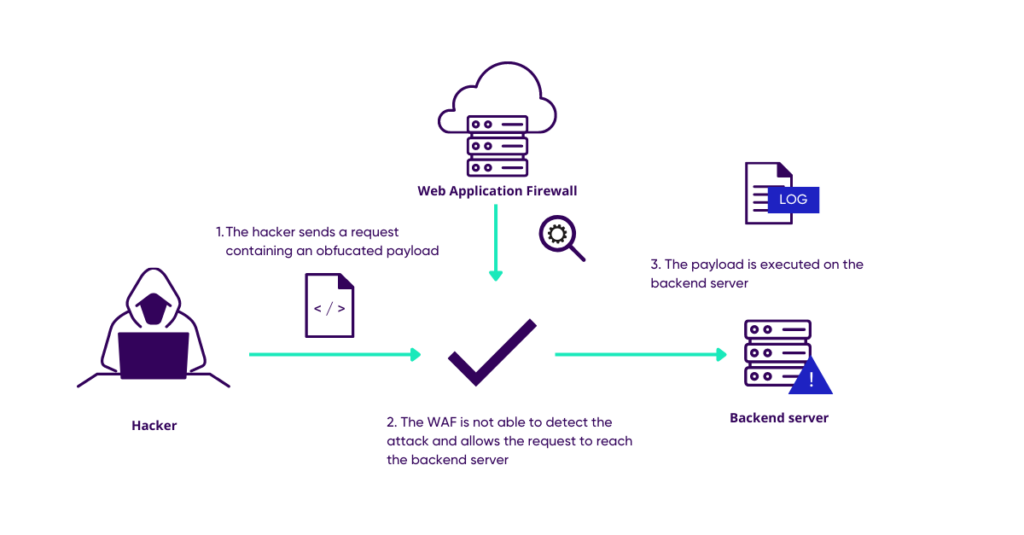
Layered obfuscation: a taxonomy of software obfuscation techniques for layered security | Cybersecurity | Full Text
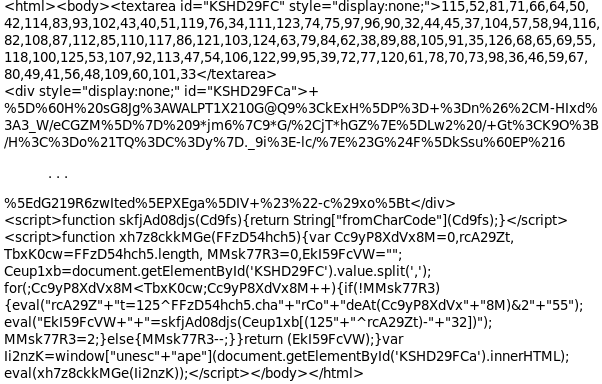
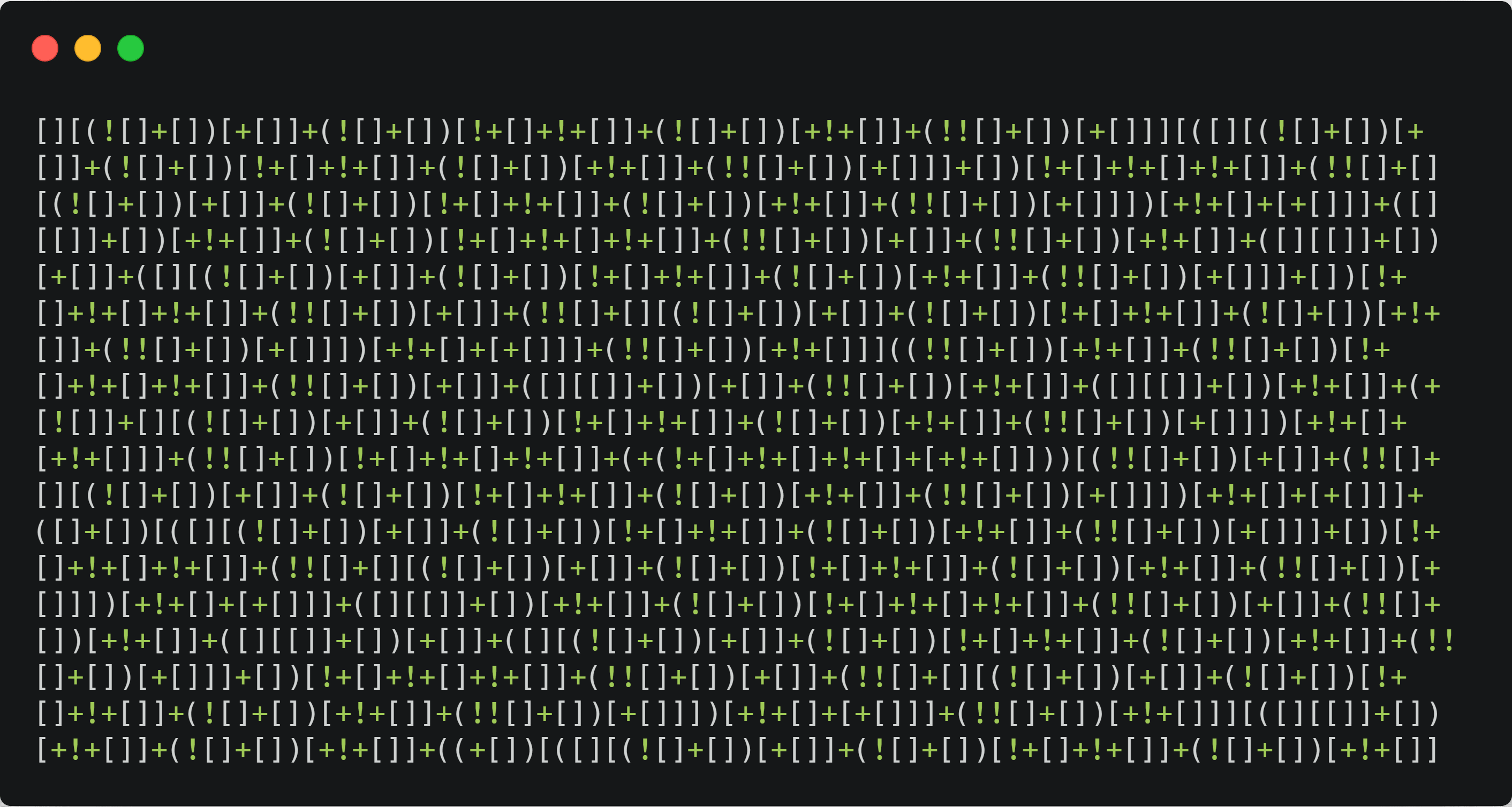
De-obfuscating javascript code in Chrome Developer Tools | by Sagar Ganatra | Sagar Ganatra's blog | Medium
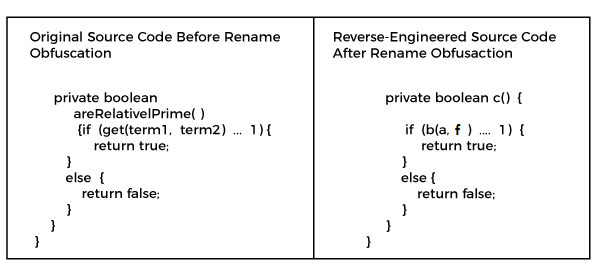



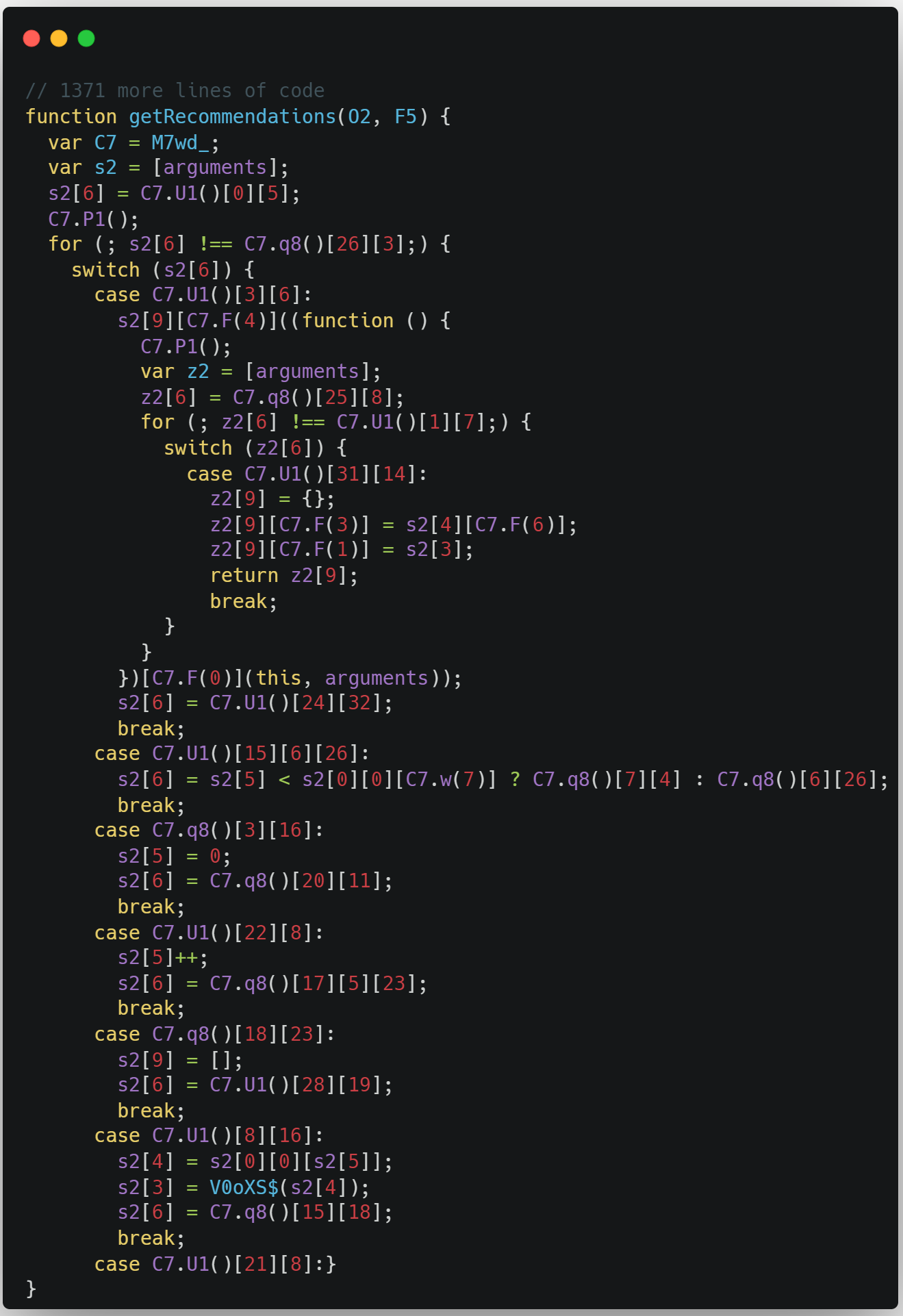
/filters:no_upscale()/articles/anatomy-code-obfuscation/en/resources/73-1667851620388.jpeg)



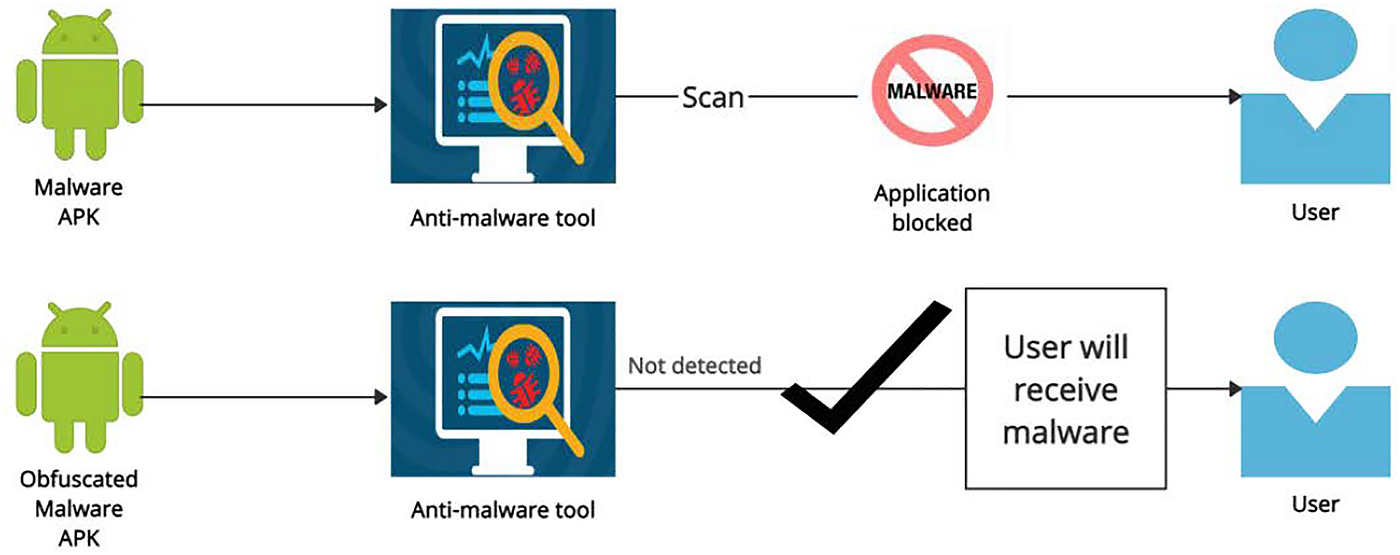
![On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ] On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-1002/1/fig-3-2x.jpg)